- About
- Services
COMPLIMENTARY WORDPRESS MIGRATIONS.
Our Free WordPress migrations include zero-downtime. We work closely with you ensuring the migration is as smooth as possible.
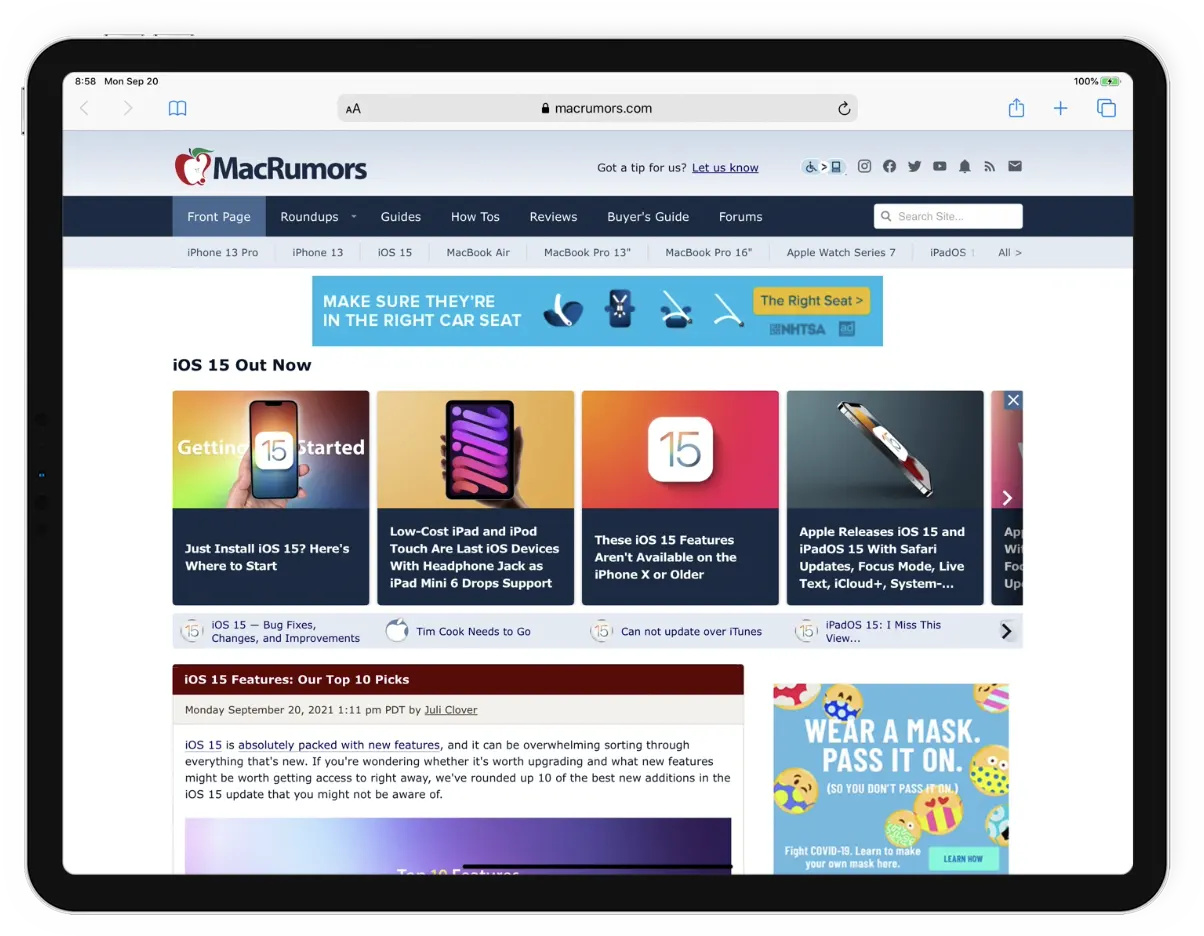
After implementing Host Duplex’s optimization and scaling technologies, MacRumors observed a 200% increase in performance (decreased page load time) over SoftLayer/IBM. While traffic has increased 7.7x since 2015, Host Duplex’s optimization, scaling technology, and added efficiencies have allowed their cloud costs to remain stable.
- Pricing
- Case Studies
- Help
Read how Host Duplex customers describe their experiences with our support, hosting services, and our response time.
Exceptional Hosting.
Secure. Fast.
Trusted by leading organizations.
Tailored caching + LiteSpeed
Magento, WordPress, and XenForo centric

The Fastest
Magento Hosting.
Secure. Scalable.
Trusted by leading organizations.
Custom Clusters + Magento =
Blazingly fast Magento web sites

Understanding your performance issues unlocks your potential
97%
of customers see an improvement in performance.*
Faster sites =
More revenue.
97% improved site load time
91% improved CMS backend speeds
88% improved PageSpeed scores
93% improved uncached page speed
*WebPageTest.org results after staff migration.
Partner with the Pros: Leading companies trust our experts
Our staff has been acknowledged for their work by some of the biggest names in business.
Additional features
100% renewable energy match
We acknowledge the impact data centers have on the environment. From designing our servers and racks with efficiency in mind, we are are fully committed to being eco-friendly. We offset 100% of our data center energy usage via renewable energy credits (RECs).
DuplexGuard
Security
Keeping you safe from the evolving security attacks of today is of utmost importance. At Host Duplex, we’ve created a penta-layer firewall to prevent and protect you from 99% of attacks.
SSD
Platform
WP Business, Premier Cloud and Enterprise feature Pure SSD drives. This means you achieve the fastest performance using our fastest RAID arrays, translating to faster site response and performance.
Litespeed
cache
For the ultimate performance and response time, we deploy LiteSpeed Cache which offers the lowest TTFB (Time To First Byte) with the highest amount of requests per second. Read how MacRumors uses LiteSpeed to achieve 3000 requests per second.
Additional features
100% renewable energy match
We acknowledge the impact data centers have on the environment. From designing our servers and racks with efficiency in mind, we are are fully committed to being eco-friendly. We offset 100% of our data center energy usage via renewable energy credits (RECs).
Litespeed
cache
For the ultimate performance and response time, we deploy LiteSpeed Cache which offers the lowest TTFB (Time To First Byte) with the highest amount of requests per second. Read how MacRumors uses LiteSpeed to achieve 3000 requests per second.
DuplexGuard
Security
Keeping you safe from the evolving security attacks of today is of utmost importance. At Host Duplex, we’ve created a penta-layer firewall to prevent and protect you from 99% of attacks.
SSD
Platform
WP Business, Premier Cloud and Enterprise feature Pure SSD drives. This means you achieve the fastest performance using our fastest RAID arrays, translating to faster site response and performance.
Additional features
100% renewable energy match
We acknowledge the impact data centers have on the environment. From designing our servers and racks with efficiency in mind, we are are fully committed to being eco-friendly. We offset 100% of our data center energy usage via renewable energy credits (RECs).
Litespeed
cache
For the ultimate performance and response time, we deploy LiteSpeed Cache which offers the lowest TTFB (Time To First Byte) with the highest amount of requests per second. Read how MacRumors uses LiteSpeed to achieve 3000 requests per second.
DuplexGuard
Security
Keeping you safe from the evolving security attacks of today is of utmost importance. At Host Duplex, we’ve created a penta-layer firewall to prevent and protect you from 99% of attacks.
SSD
Platform
WP Business, Premier Cloud and Enterprise feature Pure SSD drives. This means you achieve the fastest performance using our fastest RAID arrays, translating to faster site response and performance.
event DAYS ARE A THING OF THE PAST
Delivering a blistering 3000 requests per second

Optimization efficiencies have allowed 7x traffic without increasing costs.
event DAYS ARE A THING OF THE PAST
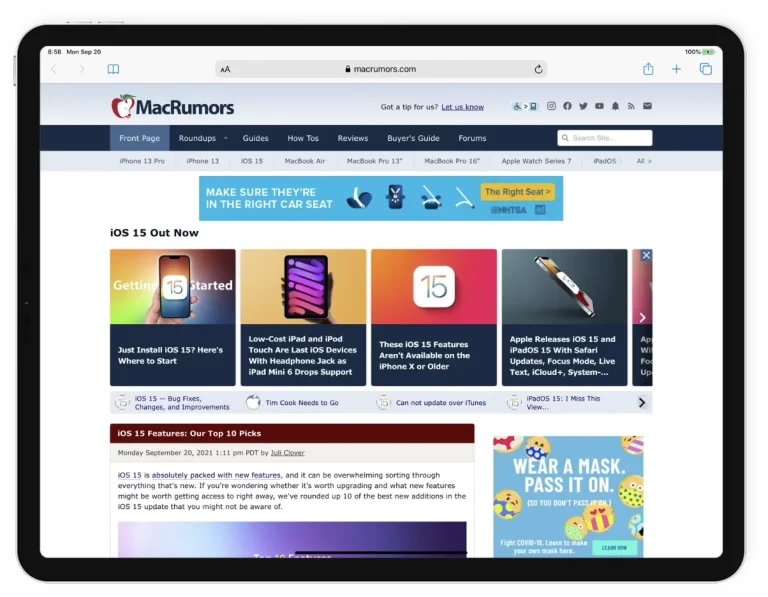

Optimization efficiencies have allowed 7x traffic without increasing costs.
How it works.
Meet your Account Manager
Online or over Zoom, we take the time to learn all about your requirements and your business.
Get your results
In-depth performance testing tells us even more about you so we can create a plan to help improve your speeds.
Start your plan.
We'll provide a plan outlining clearest path forward with on-going support to help your business succeed.
How it works.
Meet your Account Manager
Online or in-office, we take the time to learn all about your requirements and your business.
Get your results
In-depth performance testing tells us even more about you so we can create a plan to help improve your speeds.
Start your plan.
We'll provide a plan outlining clearest path forward with on-going support to help your business succeed.
client testimonials
The HD team worked tirelessly to ensure our forums and front page stayed up during Apple event days.

As a company in the market of ecommerce, being there for 24/7 has been the key point and Host Duplex is always there for us when we needed. They recently helped us surpass our sales goals by increasing our Magento performance several fold.

Thanks to Sam and everyone @HostDuplex for keeping Canon Rumors up and running over the last 24 hours. #TheBestHost

The problem with WordPress is that you can easily slow it down... when I was migrating it over, Host Duplex helped me optimize it, make it faster, and work more seamlessly.

In my industry, you hear a lot of horror stories about web hosts, I just want to let everyone know that there are still some great companies out there and HD is DEFINITELY one of them.

Play Video about Testimonials Thumbnail